Internet Educational Series #7: Firewalls & NAT
How can we protect our computers from hackers while browsing the Internet without exposing ourselves?

You know the internet uses IP addresses to identify the devices where it has to send the packets and overall data. However, as time has passed, the number of available IP (version 4) addresses is almost exhausted and something had to be done to reuse or at least optimize the use of addresses.
Additionally, as more people learnt about the internet, and more and more files were uploaded to the net, serious threats appeared which had to be addressed.
In this article we’re gonna talk about how do our home devices (the ones connected to our home network, which is supposed to be secure) are connected to external networks such as the Internet (which are supposed to be “insecure”), and how do we protect our networks and devices from bad actors.
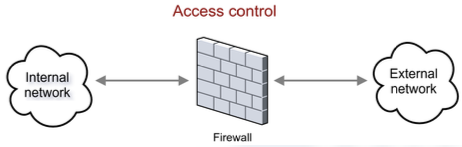
Firewalls
Usually routers distribute traffic according to a set of rules that only accounts for the destination address.
They do forward packets through a specific gateway (the default one, or another one that we must indicate) to the destination device.
But what if the traffic needs to be controlled according to other parameters?
For example imagine we are implementing the network of a certain company, and they ask for the following requirements:
- Equipment in the external network can only access the public web server.
- However, the marketing department can access the private web server, BUT not the public one.
- Traffic from one, and only one, specific device in the external network can reach the marketing network.
- Traffic going out the intranet network cannot reach the external network.
A possible solution would be to configure each single device to receive and send only the desired packets.
However this is not at all a scalable solution, and so another method had to be used. And this method are the FIREWALLS.
A firewall can be understood as a toll for control access.
It splits the network topology into an internal network, which should be secure and trusted, and an external network, which is somehow untrusted.
Goals of Firewalls
Firewalls are implemented generally for the following points, however they can have multiple other use cases.
- Single choke point for network traffic. This gives a solution to the scaling problem, and minimizes the risk.
- Access control rules. Only authorized traffic will be allowed to pass the firewall. This eases the administrative work.
- Secured Devices.
Types of Firewalls
1. Packet Filtering Firewalls
Packet filters inspect the IP packets reaching the Firewall and apply a set of rules to decide if they are forwarded or discarded.
- ACCEPT/FORWARD
- REJECT
- DROP
Filtering rules are based on information contained inside a packet, such as the network source/destination addresses, the transport source/destination addresses (TCP/UDP ports), the protocols used and the incoming/outgoing network interface.
Advantages:
- Simplicity
- Fast Evaluation
- Doesn’t change the traffic flow or characteristics
Weaknesses:
- Limited auditing
- Vulnerable to several (simple) attacks (spoofing attacks, source routing attacks, tiny fragment attacks…)
2. Stateful Filtering Firewalls
Also called Dynamic Packet Filtering, it takes into account the context, i.e. it maintains a history of previously seen packets to make better decisions about future packets.
It tracks open connections, maintains a table of them, and associates new connections requests with existing legitimate connections.
When tracking the open connections, the firewall maintains the following attributes (among others):
- IP addresses
- Ports
- Sequence numbers
- Connection Status
Advantages:
- More secure
- Defense against spoofing and DoS attacks
- Prevents TCP sequence-numbers attacks
Weaknesses:
- Rules are harder to write
- Still limited auditing capabilities
3. Proxy Firewalls
Proxy firewalls, or Application layer gateways (ALG) are devices that act as a relay for application-level traffic.
This means they can “understand” certain traffic application protocols. They are able to detect:
- If an unwanted protocol is attempting to bypass the firewall on an allowed port.
- If a protocol is being abused in any harmful way.
- If user credentials are enough to use some protocol.
Advantages:
- Even more secure
- Full auditing capabilities
- Hides the internal addressing scheme
- Harmful applications can be blocked
Weaknesses:
- Usually slower as they require much more resources
- A comprehensive knowledge of the protocol is needed
- Not available for all the application protocols
- Application protocols update frequently, and so the proxy has to be updated too
- Sometimes some extra client configuration is required
NAT
So now that we know how to protect ourselves from “external insecure networks”, we should know how to reach them.
But, you already told us that to reach a device we only need to know its IP address isn’t it? Yeah, that’s it.
However, you may have seen that MANY devices have really similar addresses between them, like the typical 192.168.1.1 (usually your home router).
This is because as the Internet grows bigger and bigger, the different networks which form the whole net had to find a way to differentiate between them.
There are PUBLIC networks and PRIVATE networks, being the first ones accessible for everyone, but the latest ones only for the ones who are inside that network.
Note how everyone can access directly the public addresses, but not the private ones.
For this exact reasons, almost ALL private networks use the same range of addresses (usually C class range, 192.168.0.0/16), as each and every private network is just accessible from its inside hosts, and they don’t need to have a different address from an unreachable host, as they are not connected from the first place.
Let’s put an example: We have 2 companies, A and B.
All the devices from network A can only access other devices from its internal network, but not the ones from B. This way, we can assign the same exact address to a device from network A and network B, as there will be no confusion between them.
That sounds legit, but what if now we need to connect from a certain device from network A to network B? Or maybe we want to send something from a private address to a public one.
We must know how to reach all this addresses.
This is when the NAT comes into play. It stands for Network Address Translation, and it is a mechanism that translates IP addresses (and port numbers), and allows to connect public and private networks, saving public IP addressing this way.
When we use NAT, two address translations are performed:
- One when the packet departs the NAT router.
- The reverse translation when the packet returns to the NAT router.
NAT Types
To do so, we use two main types of NAT.
Source NAT (SNAT):
- The router translates the source address after routing, just before the packet leaves the router.
- When response packets arrive, the router will perform the reverse operation (translation of destination address).
Destination NAT (DNAT):
- The router translates the destination address before routing, just when the packet arrives to the router.
- When response packets arrive, the router will perform the reverse operation (translation of source address).
Consequences of NAT usage
If IP addresses change, the checksums must be recalculated.
When a NAT is used, response packets should return to the same NAT router (to perform the reverse translation).
For this reason, in most cases there is only one NAT router to manage the Internet access.
NAT Limitations
For the above reasons, when using NAT, the Internet becomes a pseudo-connection-oriented network.
Furthermore, each NAT router becomes a bottleneck, as it must manage the translation of all ingoing and outgoing connections.
In case the router does also need to use a proxy firewall (ALG), it will have to do a whole bunch of tasks before sending each packet.
NAT conclusions
So forth, NAT has been extending the lifetime of IPv4, delaying IPv6 deployment. However, this is far from being an optimal solution, as there can be different behaviors for different NAT implementations, and new applications will need extra NAT support.
Firewalls & NAT in Linux (IP tables)
Alright, now you know the theoretical approach to how we connect to external devices, and how we protect ourselves from malicious actors.
Let’s take that into practice and see how we can implement NAT in Linux systems.
Netfilter
Netfilter is the packet filtering framework used in Linux platforms.
It contains chains of rules for the treatment of packets.
Each chain is associated with a different “role” of the host when processing packets.
Each network packet arriving at or leaving from the computer goes through at least one chain.
The five predefined chains are the following ones:
- PREROUTING: First chain that a packet finds when it comes from the network. It is located before the routing decision.
- INPUT: This chain applies when the packet is going to be locally delivered (the host is the destination), and it must perform some action in the host itself.
- FORWARD: the packet will enter this chain if it comes from the network, but the host is not the destination.
- OUTPUT: this chain applies when packets are sent by the host after having performed some action, and they need to be sent to another host.
- POSTROUTING: The packet will enter this chain after the routing decision has been made, and it will send the packet further.
Netfilter syntax
When a packet enters a chain, the kernel verifies if the rules inside the chain match this packet to know how to proceed.
Each rule contains some specifications to decide if the packets match it.
If a packet reaches the end of the chain without matching any rule, the default chain policy is applied (for example DROP).
How to configure the netfilter chains in the Linux Kernel? Using the iptables command.
Syntax:
iptables <table> <op> <chain> <pkt-match-condition> <action>- table: Selects the table to work with
-t filter: selects packet filtering
-t nat: selects NAT table
- op: Rule operations within a chain
(-A) APPEND a new rule to the chain
(-I) INSERT a new rule in a position within a chain
(-D) DELETE a rule in a position within a chain
(-R) MOVE a rule from a position to another one
- chain: the chain name to operate with
Packet filtering: INPUT, OUTPUT and FORWARD
NAT: PREROUTING, POSTROUTING and OUTPUT
- Packet Matching Condition: The set of conditions that a packet must satisfy. There are 3 types of conditions:
Physical/link layer conditions: network interface where the packet is received/transmitted.
Network layer conditions: fields in the IP header
Transport layer conditions: fields in the transport header
- Action: The verdict is applied to the packet if all the rule conditions are satisfied.
Conditions:
- for the PHYSICAL/LINK layer:
-i, --in-interface [!] name
-o, --out-interface [!] namenames of the interface via which packets will be received/sent
- for the NETWORK layer
-p, —protocol [!] protocol The protocol of the packet to check. It can be tcp, udp, icmp, or all
-s, —source [!] address[/mask] Source specification (network name, hostname, @IP…)
-d, --destination [!] address [/mask] Destination specification.
- for ICMP (if
--protocol icmpis specified in the conditions of the network layer)
--icmp-type [!] typename This allows specification for the ICMP type
- for TRANSPORT layer (if
--protocol tcpis specified in the conditions of the network layer)
--source-port [!] port[:port]
--destination-port [!] port[:port]
--tcp-flags [!] mask comp
As you can see there are many options available for the <condition> field, as the above ones are not all of them yet, but the main ones.
Examples
Finally I’ll show you some example of the iptables command and its use:
- Adding a rule in the INPUT chain to drop packets whose source IP address is 192.168.1.1 and transport protocol is TCP:
iptables -t filter -A INPUT -s 192.168.1.1 -p tcp -j DROP- Adding a rule in FORWARD to drop packets whose source IP addresses are in range 192.168.1.0/24, the protocol ICMP and icmp type echo-request, and received in the eth0 network interface:
iptables -t filter -A FORWARD -i eth0 -s 192.168.1.0/24 -p ICMP --icmp-type echo-request -j DROP- Adding a rule in OUTPUT to avoid outgoing http connections towards the www.google.com server:
iptables -t filter -A OUTPUT -d www.google.com -p tcp --dport 80 --syn -j DROP- Adding a rule to do SNAT for all packets that leave the router using the eth1 interface, translating to the IP address 172.16.1.1:
iptables -t nat -A POSTROUTING -o eth1 -j SNAT --to 172.16.1.1I know at first the rules used in our computers to filter the traffic can be a little hard to grasp, however once you have an overall understanding of how the whole Internet works, everything becomes much more clear.
In case you want to learn more about this topics, feel free to check my previous articles:
- Chapter 1: Ethernet, Switching & VLANs
- Chapter 2: IP Basics
- Chapter 3: Network Apps
- Chapter 4: DNS
- Chapter 5: DHCP
- Chapter 6: WWW (HTTP(S), HTML, Cookies…)
Finally, this series will reach to the 10th episode, so if you’ve liked my content please leave a clap, it makes a huge difference for me and keeps me motivated to write more articles!